Managing Your Data Life: Navigating SSO Vulnerabilities
Written on
Chapter 1: Understanding SSO Vulnerabilities
The internet serves as a vast reservoir of resources. Social media scrolling has become a common indulgence, while AI-powered tools are touted as essential aids in decision-making that many of us never asked for but now rely on. As the tech industry continues to debate the advantages and disadvantages of AI tools and platforms, the average user is left to navigate the data they share with these systems.
When these digital identity providers or their parent companies face network issues, customers are often unable to access the services offered by various companies. This disruption halts all communication between businesses and their clients. Many believed that such a worst-case scenario was unlikely to occur, but it did. On October 4, 2021, platforms like Facebook, Messenger, Instagram, and WhatsApp were down for nearly six hours. The fallout was more than just missed social media updates; every company relying on Single Sign-On (SSO) to facilitate interactions with clients and employees was suddenly cut off from effective communication. During this outage, Twitter became an informal channel for keeping both personnel and customers updated on the status of the services.
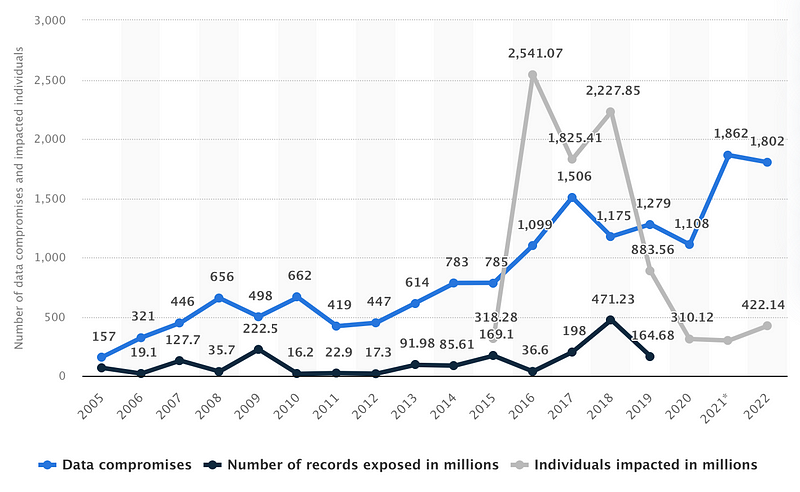
The primary benefit of SSO—the convenience of using one set of login credentials—also contributes to its main vulnerability. Essentially, SSO functions as a universal credentialing protocol, which increases the risk to both sensitive and non-sensitive data during a data breach. The likelihood of falling victim to such breaches is on the rise; in 2022 alone, Statista reported that over 422 million individuals were affected. The frequency of data breaches has steadily increased since at least 2005, as highlighted in the accompanying Statista chart, with a continuous list of incidents available through Firewall Times.
Chapter 2: Protecting Your Digital Footprint
While these statistics can be alarming, there are proactive measures you can take to safeguard your data. Here are three strategies to help you exercise your data agency:
Know Your Rights Regarding Data Breach Notifications
In the U.S., all 50 states, along with the District of Columbia, Puerto Rico, Guam, and the Virgin Islands, have implemented laws mandating data breach notifications. California set the precedent as the first state to enact such laws in 2002. Organizations are required to inform affected individuals when their personal identifying information (PII) may have been compromised, ideally within 30 to 60 days. If you receive a “Notice of Data Breach” letter, it should include details on what transpired, the information at risk, corrective actions being taken, and guidance for affected individuals, along with contact details for further inquiries. For a comprehensive checklist, refer to the U.S. Federal Trade Commission’s IdentityTheft.gov, which outlines actionable steps. Some companies may also offer a year of complimentary credit monitoring or additional support if your government-issued number has been compromised.
Limit Your Use of Single Sign-On
Although SSO simplifies online access, you often have the option to bypass this feature. Creating unique usernames and passwords for each platform may require more management on your part but can significantly enhance your security. This approach prompts you to reassess whether joining another online service is truly necessary. Alternatively, you can set up a new user profile with the same username but a different password for each platform.
Minimize Data Shared on SSO Platforms
If you must use SSO, consider limiting the amount of information you provide. For example, fill out only the mandatory fields and refrain from sharing your full name, birthdate, credit card information, or profile picture. Providing minimal information makes it harder for malicious actors to exploit your data. Adopt the mindset of “If they take it, it’ll cause me little to no harm.”
Navigating the complexities of the digital world is an ongoing challenge. While we cannot control all aspects of our online presence, we can take proactive steps in areas where we have the power to influence our data security.
Explore foundational concepts in data and analytics that can empower you for real-world projects.
Learn essential data management principles and best practices to protect your information effectively.