Harnessing Nexpose for Effective Vulnerability Assessment
Written on
Chapter 1: Introduction to Nexpose
After downloading, head to the “/Downloads” folder and grant executable permissions to the file.
Example: (root@kali:~/Downloads# chmod a+x Rapid7Setup-Linux64.bin).
Then, install Nexpose by running the file.
Example: (root@kali:~/Downloads# ./Rapid7Setup-Linux64.bin).
To launch the Nexpose console, type “service nexposeconsole start.”

Chapter 2: Initiating a Vulnerability Scan
To start a vulnerability scan, click the “CREATE SITE” button on the main screen.
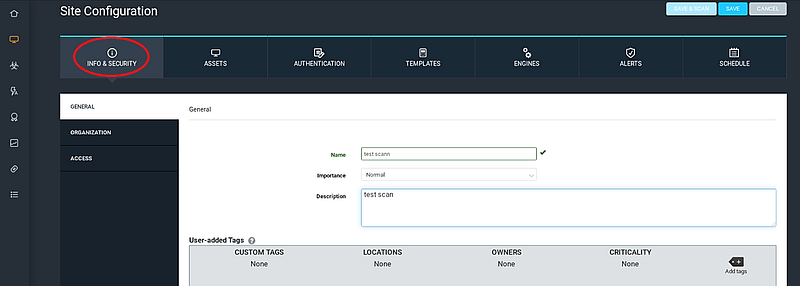
Under the “INFO & SECURITY” section, enter a name and a brief description for your target site.
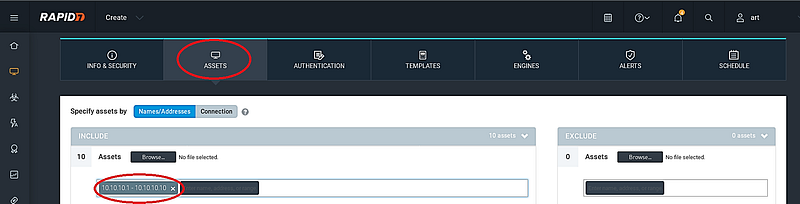
Next, navigate to the “ASSETS” section, where you will input the assets you wish to scan.
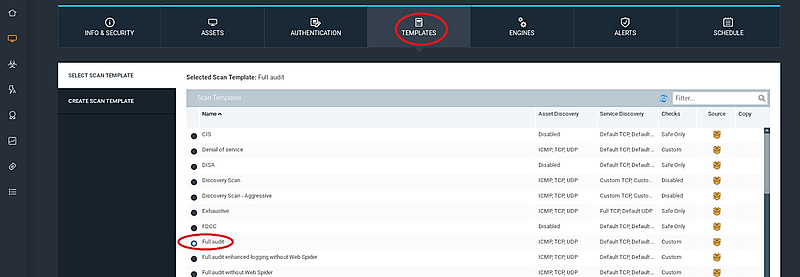
Proceed to the “TEMPLATES” tab to choose a scanning template. In this instance, we will select the “Full audit” template. Nexpose provides a variety of pre-configured templates, including those for compliance checks (like SOX and PCI) and SCADA system assessments, along with options to customize existing templates.
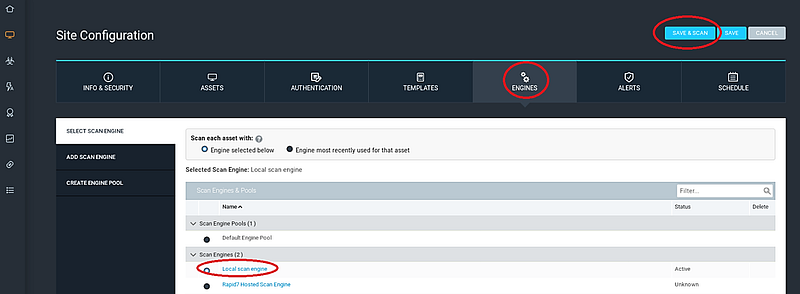
The “ENGINES” section allows you to select the scan engine for your assessment. Nexpose operates with a distributed architecture that enables deployment of scan engines in remote locations inaccessible from the main console. The Nexpose console includes a built-in scan engine, so we will opt for the “Local scan engine” option for our scan.
Now, click “Save and Scan” to initiate the scanning process. You can also visit the “SCHEDULE” tab to set up scans for future dates or to create a recurring scan schedule.
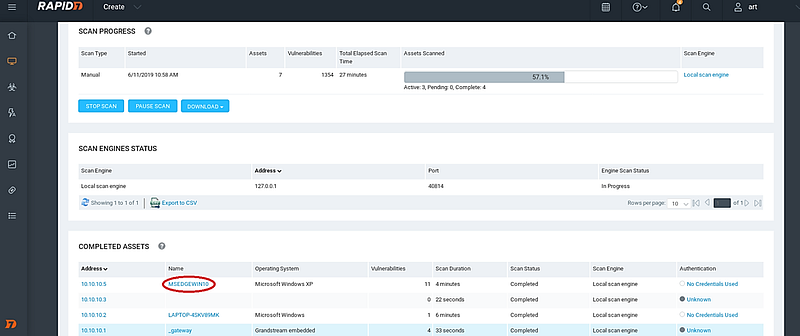
As the scan progresses, you can observe information about completed assets in the “COMPLETED ASSETS” section.
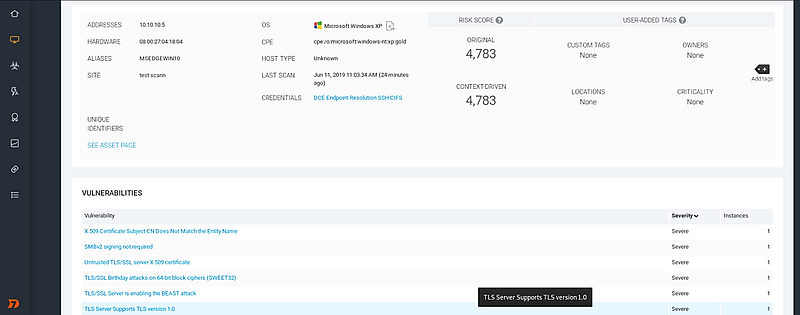
Clicking on any completed asset will provide detailed information regarding that specific target.
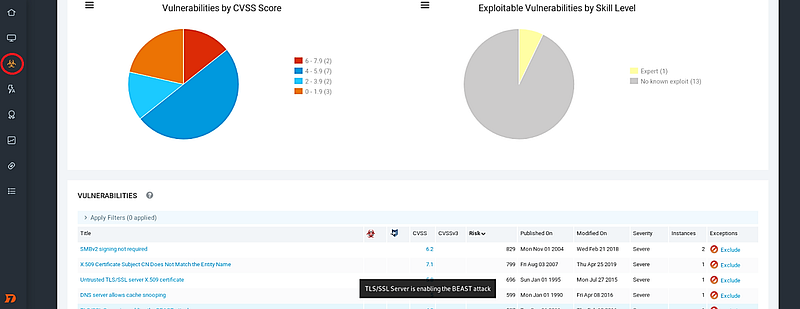
To explore all possible vulnerabilities within your network, select the “Vulnerability” icon on the left sidebar. This section categorizes vulnerabilities by severity and highlights exploits available in Metasploit, along with the necessary access levels to leverage these vulnerabilities, allowing for potential exploitation.
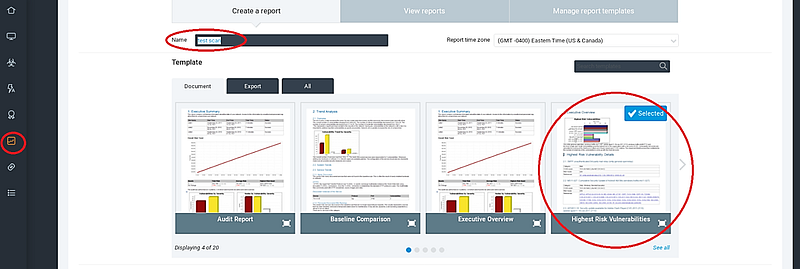
Upon completion of the scanning process, findings can be saved for review by clients or utilized for further penetration testing. Click the “Reports” icon from the left sidebar, enter a name in the “Name” field, choose your template, and save your report.
Nexpose generates a report and provides a direct link for access. Click on this link to view your report.
Vulnerability scanners like Nexpose are designed to assist security professionals in identifying potential weaknesses within their networks and systems. However, savvy hackers can also leverage these tools to pinpoint targets and their vulnerabilities. With Nexpose and similar scanners, there’s no need for guesswork; they can accurately identify not only vulnerabilities but also the corresponding exploits that could be used against them.
For further insights into red teaming, check out the video titled "Micah Zenko - Red Teaming Insights and Examples from Beyond - DEF CON 27 Social Engineering Village" which delves into practical examples and strategies.
Additionally, explore the "Ethical Hacking Crash Course Using Parrot Security OS (An Alternative to Kali Linux)" for a comprehensive overview of ethical hacking methodologies and tools.