Mastering Network Scanning with Unicornscan and More
Written on
Chapter 1: Introduction to Unicornscan
Unicornscan serves as a robust tool designed for network specialists to enhance their scanning capabilities and gauge responses from TCP/IP-enabled devices or networks. This application features an advanced asynchronous stateless TCP filtering system that can handle various TCP flags, along with asynchronous stateless TCP flag capturing. Additionally, it enables both active and passive identification of remote operating systems and applications by analyzing responses received.
For instance, upon receiving a response, the Time-To-Live (TTL) value is analyzed for each port, which can indicate the operating system in use. A TTL value of 128 typically signifies a Windows operating system.

Photo by schach100 from Pexels
Penetration testers often leverage Unicornscan when traditional port scanning techniques fall short, especially if the target has implemented port scanning detection measures, such as intrusion detection systems (IDS), intrusion prevention systems (IPS), or honeypots. A distinctive aspect of Unicornscan is its ability to utilize multiple threads for sending and receiving packets, setting it apart from other port scanners.
Unicornscan is readily available in all versions of Kali Linux; simply initiate it by typing "unicornscan" in the terminal.
Chapter 2: Executing Scans with Unicornscan
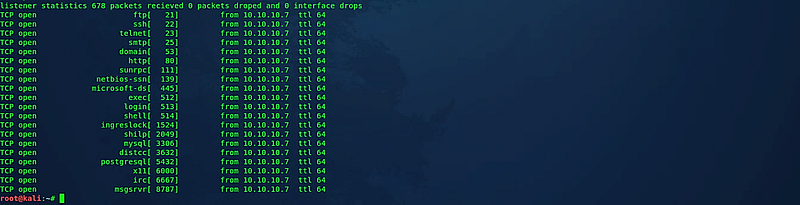
To conduct a TCP scan using Unicornscan, you can utilize the immediate mode (-I) to display results in real-time on a specified interface (-i) while employing the TCP SYN profile (-mT). For example:
(root@kali:~# unicornscan -v -I -i eth0 -mT 10.10.10.7)
This command will probe for all open TCP ports alongside their respective running services.
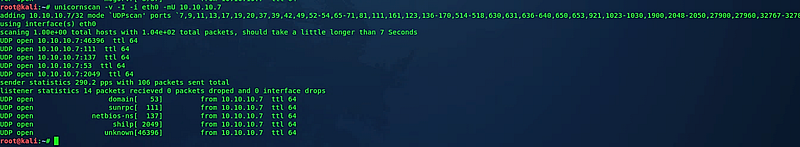
The same approach can be adapted for UDP scanning by utilizing the UDP scanning profile to identify open UDP ports:
(root@kali:~# unicornscan -v -I -i eth0 -mU 10.10.10.7)
As you conduct network scans with Unicornscan, it’s advisable to run Wireshark concurrently to observe the outgoing packets. This allows you to analyze the patterns of packet transmission employed by Unicornscan.
In the video titled "Unicornscan - Port Scanning," you'll gain insights into the operational features of Unicornscan and how it can be employed for effective network scanning.
The second video, "Ranking Port Scanners - Tier List," provides a comparative analysis of various port scanners, including Unicornscan, helping you understand their strengths and weaknesses.